F5 BIG-IP LTM v2.0
Introduction
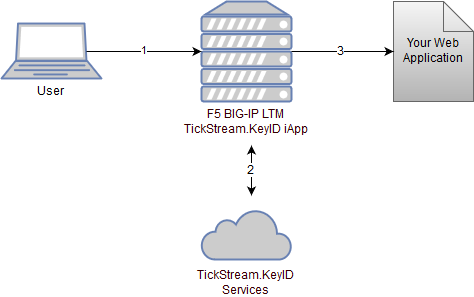
TickStream.KeyID F5® BIG-IP® LTM® is an iApp® template that allows you to provide 2nd factor authentication for F5® BIG-IP® LTM® implementations. The template creates a set of iRules® and a stream profile for protecting a virtual server resource.
The iRules® created intercept HTTP requests and responses to dyamically insert the necessary KeyID javascript and HTML hidden form tags into your application login pages. When a login is performed using an HTML post, a KeyID evaluation will be attempted and the results added to the headers or post data sent to the login form's action page.
Only login pages designed using the HTTP POST method are supported. You can use the LTMValidator helper application to find the necessary values for configuring the iApp®.
All operations are completed using traditional TCL based iRules®. This version will be deprecated in favor of the a new iRules® LX® version.
System Requirements
Except for the TickStream.KeyID Server, all needed components are self contained in the iApp® template.
- F5® BIG-IP® LTM® version 11.5 and newer
- TickStream.KeyID Server 1.9
F5 iApp Template
- Download the TickStream.KeyID F5® BIG-IP® LTM® iApp template using the link provided to you.
- Log in to the administration console for your F5 BigIP device.
- From the main menu, click iApps -> Templates.
- Click the Import button.
- Click the Browse button to locate the iApp template downloaded previously. If you are updating an existing template, check the Overwrite Existing Templates box.
- From the main menu, click iApps -> Application Services.
- Click the Create button.
- Specify a name for the particular iApp installation, i.e.
myapp. From the template drop down, choose KeyID. -
In the Webservices configuration section provide the following information:
Item Description URL The url to the KeyID REST web services with no trailing slash i.e. https://keyidservices.tickstream.local Authentication Key The KeyID licensing key. Name Server You must provide the IP address of a name server, or a virtual server configured for name services, i.e. 192.168.1.10or/common/namesrvr-vs.Log verbosity The higher the value, the more verbose the logging messages will be. Select 0for no logging. -
In the KeyID configuration section, you may adjust the defaults as necessary:
Item Description Enable passive validation Users will be always be granted access. Enable passive enrollment Profiles will be built silently on each successful login. Minimum cohesion Profiles will continue enrollment until this percentage is met, or the maximum is exceeded. Specified as a double, i.e. 70.0.Minimum efforts Minimum number of efforts to enroll. Specified as an integer, i.e. 10.Maximum efforts Maximum number of efforts to enroll. Specified as an integer, i.e. 15.Enable custom threshold Set a custom threshold for allowing access. Minimum fidelity Minimum fidelity level for allowing access. Specified as a double, i.e. 70.0.Minimum confidence Minimum confidence level for allowing access. Specified as a double, i.e. 50.0.Obfuscate Password Password characters will not be captured, instead placeholder values will be used. Set the value to false when troubleshooting. Show KeyID JavaScript alerts Show KeyID javascript alerts, not recommended in passive scenarios. Allow backspace Allow backspaces in KeyID bound input fields, not recommended as KeyID evaluation may fail. -
You must provide several values to configure the KeyID LTM® iRules®. You can use the LTMValidator helper application to find the page, form and input values:
Item Description jQuery URL Specify the URL to jquery-1.11.1.min.js (local iFile used by default) KeyID Library URL Specify the URL to keyid-verbose (local iFile used by default) KeyID-LTM URL Specify the URL to keyid-ltm.js (local iFile used by default) Response type Determines whether KeyID evaluation results will be passed as additional post information or as custom headers to the Login Page Post Login Page Absolute URL to the login page (relative to the virtual server.) This is usually the main login page itself, i.e. /index.aspx.Bind Type Choose whether to bind to a form using its ID or DOM forms index ID/Index This is the HTML form tag ID (i.e. <form id="myform"...>) or it's DOM forms index on the login page that contains the username and password fields.Form Action Absolute URL to the login page post (relative to the virtual server.) This is often another page, i.e. /login.aspxor empty left empty to post data back to the current page.Username Input ID This is the HTML input tag ID (i.e. <input id="username"...>) for the username field.Password Input ID This is the HTML input tag ID (i.e. <input id="password"...>) for the password field. -
Click the Finished button to create the application.
- From the main menu, click Local Traffic -> Virtual Servers
- Click on an existing virtual server resource that you would like to protect with KeyID-LTM.
- From the properties page, change the Configuration: dropdown to
Advanced. Change the Stream Profile setting to match the one created by the KeyID template, i.e./Common/KeyID-LTM.app/keyid-ltm-stream. Click the Update button. - From the resource page, click the Manage button in the iRules® section.
- Add the following iRules® to the Enabled selection list:
/Common/KeyID-LTM.app/KeyID-LTM
/Common/KeyID-LTM.app/KeyID-Lib - Click the Finished button.
- Using a web browser, visit your virtual server address and verify that the appropriate javascript libraries are being loaded. You can use a F5 packet capture and Wireshark to view the KeyID evaluation results being passed as HTTP post data or HTTP headers.
Logging
The KeyID F5® BIG-IP® LTM® writes logging information to the local traffic manager log. The verbosity of the logs can be changed by reconfiguring the corresponding iApp® template setting. Each log entry is prefaced by the LTM® session ID that generated it. The KeyID web services can also be configured to log authentication information to the KeyID database.
KeyID Evaluation Results
The following values are submitted as additional HTTP headers or POST data:
| Item | Description |
|---|---|
| keyid_match | Evaluation and profile are a match. Specified as boolean i.e. true or false. |
| keyid_confidence | Evaluation confidence value. Specified as double i.e. 70.0. |
| keyid_fidelity | Evaluation fidelity value. Specified as double i.e. 70.0. |
| keyid_profiles | Number of profile entries. Specified as an integer i.e. 1. |
| keyid_ready | Profile has enough entries and is ready for evaluation. Specified as boolean i.e. true or false. |
| keyid_error | String containing any error information encountered during evaluation. |