ADFS v1.2
Introduction
TickStream.KeyID ADFS is a software package that allows you to provide 2nd factor authentication for Microsoft Active Directory Service implementations. The package must be installed on each ADFS server and Forms Authentication must be used in order to capture typing efforts.
System Requirements
Installing TickStream ADFS software on-premises requires at least one physical or virtual server running:
- Microsoft Windows Server 2012 R2
- Active Directory Federated Services (configured)
- TickStream.KeyID Server 1.5
It is recommended that you configure an SSL certificate for your TickStream.KeyID Server.
It is recommended that you be able to create an internal DNS record to point to the KeyID web service, i.e. keyidservices.yourdomain.local that is resolvable by the servers in your ADFS farm.
The setup package must be run on each server in your ADFS farm. During setup, ADFS windows services will be restarted - please plan your installation outage window accordingly.
Setup Wizard
- Download the TickStream.KeyID ADFS setup package using the link provided to you.
- Run the setup package from the intended ADFS server. Press the ‘Next’ button when the welcome screen appears.
- Accept the licensing agreement. Press the ‘Next’ button to continue.
- Choose an installation location. Press next.
- Select the ADFS 3.0 MFA Provider. Press next.
- Enter the HTTPS or HTTP URL for your KeyID server installation. Include your Authentication key. Press Next.
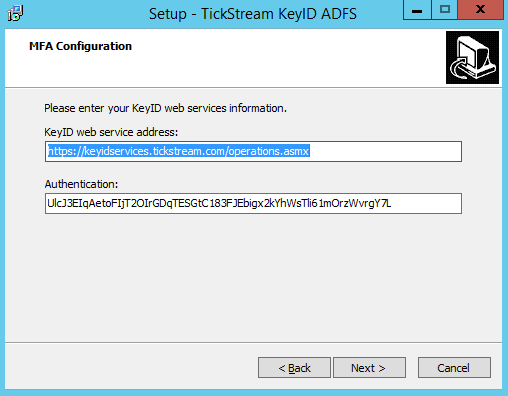
- If you are installing the TickStream MFA provider for the first time, leave this page blank and click ‘Next’. If you are installing the TickStream MFA provider on an additional ADFS farm server, provide the path to the private_key_encrypted.pem file, that can be found the ‘ssltools’ folder in the path where TickStream.KeyID ADFS was installed.
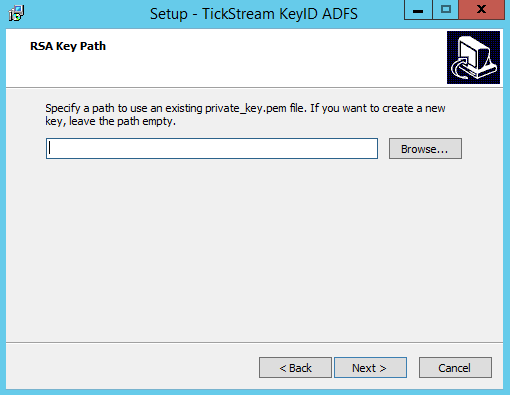
- If you are installing the TickStream MFA provider for the first time, provide a password for encrypting the private key. The password should only contain letters and numbers. If you are importing an existing private key, provide the password that was used to encrypt it. The installer does not test the password for you, be sure to type it correctly.
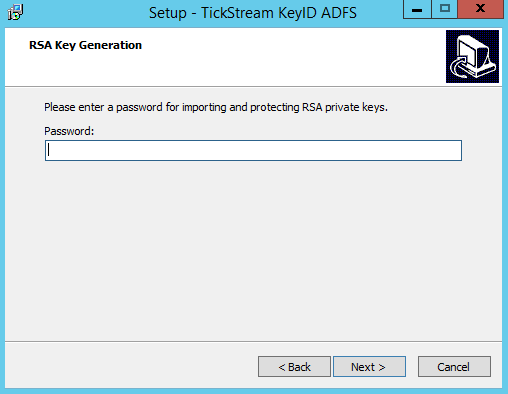
- Click the Install button to complete the installation.
Configuring ADFS
- Open the ADFS management application. Click the Authentication Policies folder. Click the ‘Edit Global Primary Authentication action.
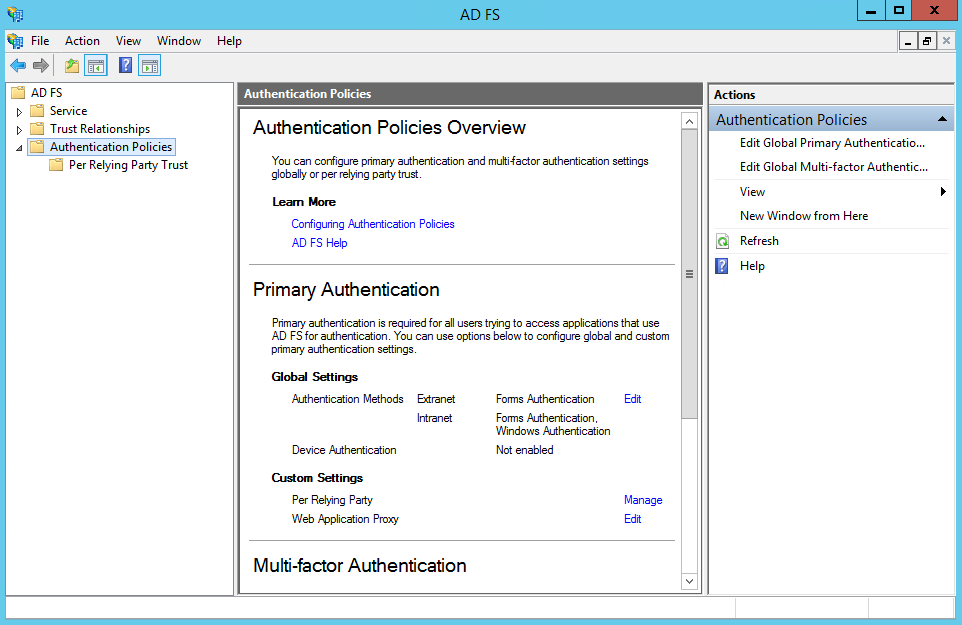
- You must enable Forms Authentication for each realm you want to protect with TickStream.KeyID.
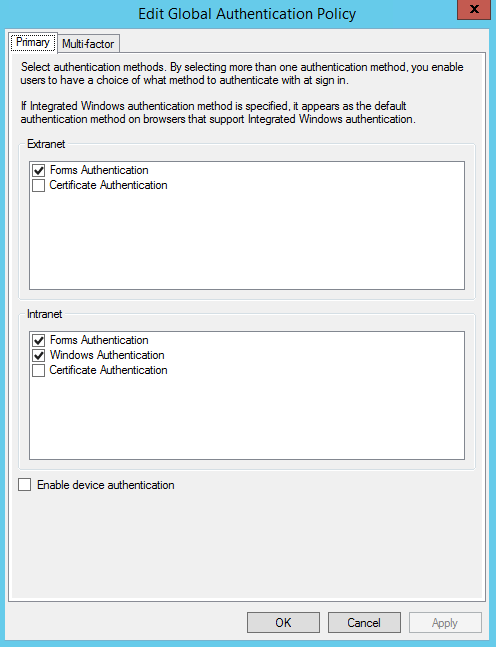
- Click the Multi Factor tab. Enable the TickStream.KeyID authentication method by checking the box, if it is not already enabled. To require multi factor authentication, you must select a user, device or location. Please note that selections are logically combined using ‘OR’. If the Extranet location box is checked, all accesses from outside the organization will require multi factor authentication, whether or not a user’s name is listed in the User/Group list. For more specific configurations, Global Authentication Policy claim rules can be customized using PowerShell. Changes will take effect immediately.
Configuring KeyID Settings
The TickStream.KeyID ADFS multi factor provider ships with ‘passive enrollment’ and ‘passive validation’ enabled by default. This means that users will seamlessly have their profiles enrolled over successive logins, and they will be validated no matter the KeyID evaluation result. This allows you to tune your installation before enforcing authentication. These settings can be changed by modifying the ADFS server registry and restarting ADFS services.
Use regedit.exe to edit the registry. The TickStream.KeyID ADFS settings are located at:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Intensity Analytics Corporation\TickStream KeyID ADFS
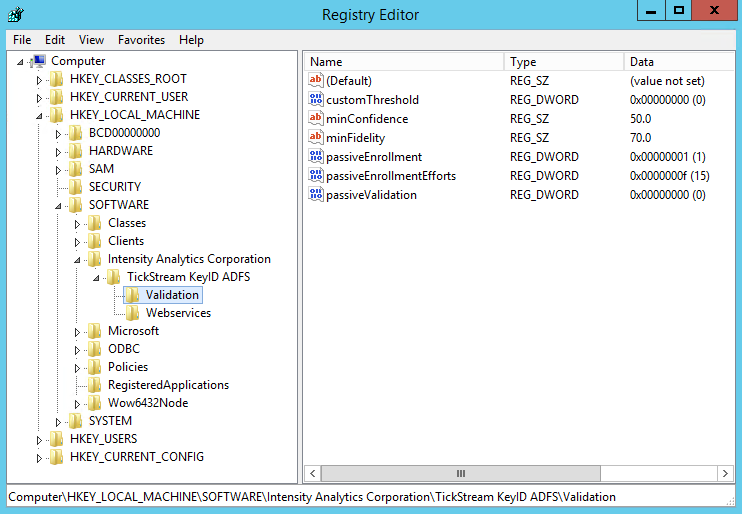
Below is a listing of configuration items and their descriptions:
| Item | Description |
|---|---|
| customThreshold | Enables a custom effort threshold for granting access. Set value to 0 to disable, 1 to enable. |
| minConfidence | Minimum confidence level for granting access. Set value as a double precision number, i.e. 50.0 |
| minFidelity | Minimum fidelity level for granting access. Set value as a double precision number, i.e. '70.0' |
| passiveEnrollment | Enables passive enrollment. Set value to 0 to disable, 1 to enable. |
| reqEnrollmentEfforts | Number of enrollment efforts to complete a profile. Set value as an integer, i.e. 15 |
| passiveValidation | Enables passive validation. All efforts granted access. Set value to 0 to disable, 1 to enable. |
| nonceLifetime | Determines how many minutes a nonce is valid for, if left unused. This should be equal to your configured ADFS SSO token timeout value. The default is 600 minutes (10 hours). |
| strictSSL | Determines whether web service calls enforce strict SSL certificate checking. Set value to 0 to disable, 1 to enable. |
| grantOnError | Allows access even if there are errors or exceptions when authenticating. Set value to 0 to disable, 1 to enable. |
| writeMonitor | Writes effort and authentication data to web service for future analysis. Set value to 0 to disable, 1 to enable. |
Encryption Keys
The login page provided by ADFS restricts what information can be passed to the logon process. In order to provide a seamless login experience, keystroke effort must be captured and stored in an encrypted cookie so that it may be posted to the ADFS MFA authentication page.
Using a RSA public key, a randomly generated password is encrypted that only the ADFS server(s) can decrypt, with their respective private keys. The effort data is then encrypted using AES 256, ensuring that it is protected at rest and in flight. The cookie is deleted on use and expires after 3 minutes.
RSA public and private keys are stored in the system registry on the ADFS server(s). The registry key permissions are set to only allow the ADFS service account and Administrators group to access them. The private key should be appropriately guarded. An encrypted copy of the private key is generated in the ‘ssltools’ folder for easily exporting and importing the key during installation.